Blog
You Might Also Want to Read
6-Step Security Checklist for Social Media
Best practices for restaurant owners & operators Social media marketing for restaurants offers enormous benefits to increase profits and build brand awareness. While many clients may tend to focus on messaging, promotions, and growing their brand awareness, there are also a few critical housekeeping tasks that should be done properly to ensure that you maintain ownership of your brand and social media properties. In addition, businesses must also be concerned with security with regards to their online presence. In this blog, we uncover the 6-foolproof steps to securing your social media channels. If you have yet to set up your…
Alfred Goldberg November 27, 2017 (Updated on February 6, 2024)- 2 min read
Best practices for restaurant owners & operators
Social media marketing for restaurants offers enormous benefits to increase profits and build brand awareness. While many clients may tend to focus on messaging, promotions, and growing their brand awareness, there are also a few critical housekeeping tasks that should be done properly to ensure that you maintain ownership of your brand and social media properties.
In addition, businesses must also be concerned with security with regards to their online presence. In this blog, we uncover the 6-foolproof steps to securing your social media channels. If you have yet to set up your social media channels and want some in-person guidance, contact the Tampa social media marketing team at Absolute Marketing Solutions today!
Identify compromises
For businesses as well as individuals, they may not recognize that they have been subjected to a case of an online breach. Perhaps you’ll discover that your Facebook business page contains posts that you didn’t publish, or a customer will tell you that you sent them a strange message. These are all familiar scenarios for businesses that have been compromised, but the first step is in recognizing where the compromise has occurred.
Websites such as haveibeenpwned.com allow you to search for a username or e-mail and check if they’ve been compromised by a data breach. The site also provides information as to the name and date of the breach. This can be useful if you monitor your email accounts closely, and you can even set up an alert to be notified. If you are the subject of a breach, make sure to change your password immediately, and remain vigilant if you see anything posted on your behalf without your consent.
Verified accounts
Verified accounts are social media accounts whose source, name, and identity have been confirmed and vetted by the social media platform. Donning a special badge, it represents that the profile is trusted by Facebook, Twitter, or wherever it appears.
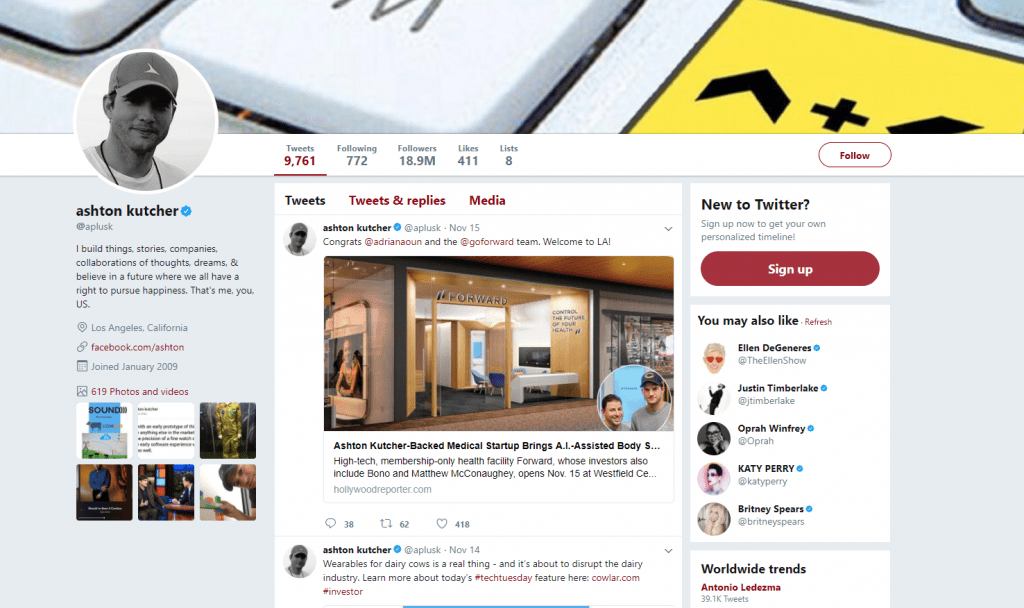
While many celebrities deal with impersonations, brands and restaurants should also concern themselves with verifying their accounts. As you can see below using the example of Ashton Kutcher, the checkmark next to his profile indicates which is the true, authentic account for the actor and entrepreneur.
Real:
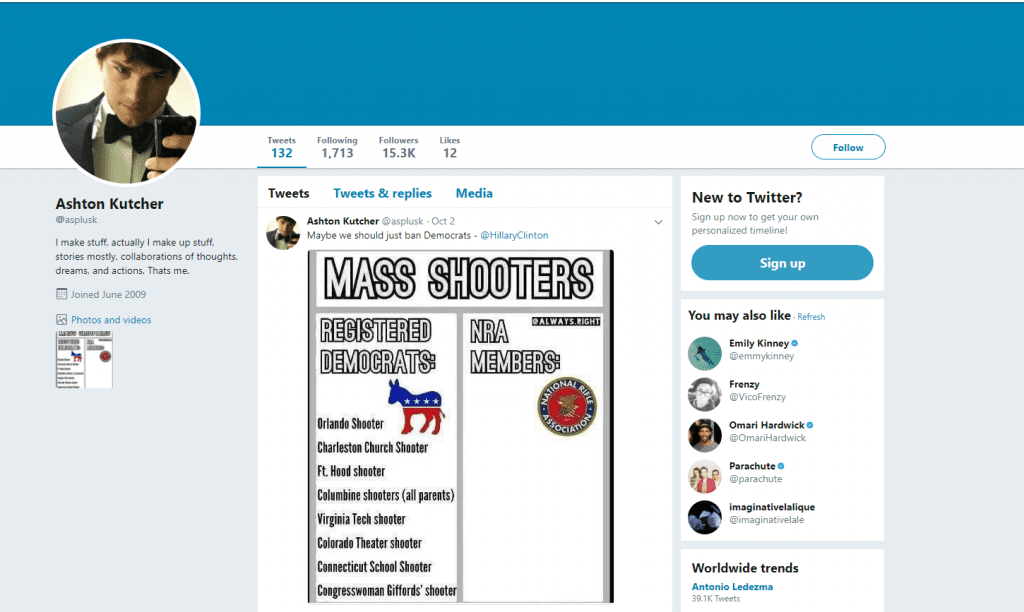
Fake #1
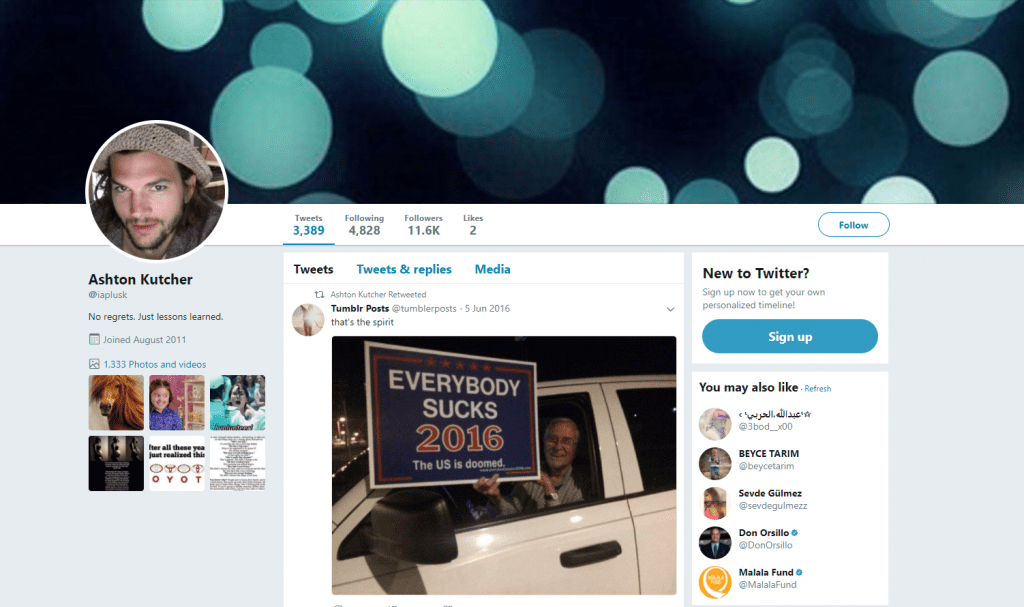
Fake #2
Depending on the size of your company, you may elect to go for a verified account whenever and wherever possible. Facebook and Twitter have various instructions for accomplishing this, mostly they involve submitting a valid form of a government ID to verify your identity. Having the badge next to your name on social media can not only make you feel more secure that your identity is not being compromised, but it will also build trust with your audience.
Multi-factor authentication
Enabling multi-factor authentication is highly recommended not only for business owners but individuals as well. Securing your email accounts, social media profiles, and business profiles with two-factor authentication could potentially save you from hardship in the future if someone attempts to hack into your account.
Two-factor authentication works by requiring verification on two devices. Usually, this is through your email address or username, paired with a mobile phone number. This way, if someone manages to discover your username and tries to log into your account, they’ll also need the code from your mobile phone to get access. Multifactor authentication is a step to better protect your brand, and reduce fears of online piracy and identity fraud, and is now employed by a vast majority of the largest social media networking sites.
Monitoring spoofs & impersonations
We recommend regularly Googling your business’ name and keeping track of the search engine page results (SERPs) to identify if other individuals or organizations are impersonating you. Even if the intent isn’t to damage your brand, they present a danger to you by not being under your control. (If you scroll back up, you’ll see how Ashton Kutcher has two Twitter accounts closely resembling his own, unfortunately, the impersonated accounts are used to disseminate jokes of a political nature which may not reflect his own opinion.)
Many popular brands inspire fan pages, parody accounts, and groups, such as Nihilist Arby’s, and Bill Bye Tho. Many official fan pages will have verified accounts too, to encourage followers to select them rather than another account. It is a good practice to be aware of these groups online and if beneficial for your brand, engage with them.
Train your employees on spotting and reporting abuse
Depending on the technical savviness of your staff, you may have employees who are active on social media. Encourage them to follow your business’ social media pages, and instruct them on how to report abuse if they discover it. We recommend that administration of social media accounts is limited to one or two senior members of your marketing or sales team, to maintain consistency in brand tone and messaging.
Use multiple passwords
While this may seem like a pain, at a time where people have dozens of passwords, never re-use the same password twice as a rule of thumb. You may consider using a password manager to keep your credentials organized and safely stored in a convenient manner. As a best practice, attempt to limit sharing passwords within your organization, and elect to create separate usernames and accounts for other people who have administrative access to your social media accounts.
What to do if your social media accounts have been hijacked.
If you are reading this blog because you have been the victim of an account hijacking, remain calm. Everyone and anyone can be the target of a hack, so don’t think that you’re the only company or person to go through this. There are a few remedies you can take immediately if you discover that your account has been hijacked.
If you’re still able to log in, do so and immediately change your password. While you are in there, check that the email address listed on the account is yours, and hasn’t been updated by the hacker. If the email address has been changed, change it back to the email address you previously used. This is of paramount importance because if you leave the hacker’s email address on the account, they could simply request a new password, and the notification would go to that account.
Next, enable two-factor authentication and select the medium you would prefer. If this wasn’t set up in the first place, you may be feeling sheepish and regretting your mistake, but this is an opportunity to learn the importance of safeguarding your accounts.
If you use any third-party applications that are connected to your social media, revoke the access, especially if there are apps you don’t use or recognize. If you use a marketing automation tool such as HootSuite, you can re-add the accounts to the platform later.
If there are any offending messages on your pages, delete them, and issue a public apology.
If your situation is direr and you are no longer able to log in, still, remain calm. On Twitter, you can reset a password request if the hacker did not change the email address associated with the account. Let’s say your hacker did change the email – then you’ll have to go to Twitter’s help center and report the violation on this form. Twitter will contact you and go through the necessary steps to confirm your ownership of the account in question. Once they’ve re-instated your access, go through the above steps after logging in.
Other social media networks have similar instructions for reporting impersonation or hacked accounts. Here is a quick list here for easy access.
Reporting a hijacked account on Facebook: https://www.facebook.com/help/131719720300233
Reporting a hijacked account on Instagram: https://help.instagram.com/368191326593075
Reporting a hijacked account on Snapchat: https://support.snapchat.com/en-US/a/hacked-howto
Reporting a hacked account on LinkedIn: https://www.linkedin.com/help/linkedin/answer/56363/reporting-a-hacked-account?lang=en
Even if you have successfully reclaimed all of your pages back from your hijackers, don’t be complacent. Practice vigilance and continue to monitor your accounts to make sure that hackers do not compromise your restaurant’s social media channels.
If you want more guidance on how to leverage social media marketing for your restaurant or business, contact the team at Absolute Marketing Solutions today for a free digital strategy consultation. We have the experience and knowledge of working with restaurant owners and operators to get their brand story into the minds of their customers. Contact us today at 813 908 6862.
November 27, 2017 - 2 min read


6 Tips for Dealing with Negative Comments on Twitter